| 5 Organizational recommendations |
[German version] |
5.1 Inspection / maintenance
In order to guarantee reliable functioning of all security-related and operational equipment, functional inspections and maintenance operations should be defined and conducted either on a regular basis or as required by events but at least once a year. Every such operation should be documented.
5.2 Regular instruction / further training of employees
The implementation of these security requirements can only be ensured if all employees are familiar with them, have been made aware of the underlying corporate philosophy and are thoroughly immersed in this. Security is only possible if founded on broad-based acceptance.
It is therefore necessary to train the personnel appropriately, provide them with further instruction or as required by events and to integrate them in the security measures.
Employees should be made aware that one of the aims of the security measures is to ensure their own personal safety.
Adherence to the security requirements should be verified and documented on a regular basis or as required by events, but at least once a year. Any required improvements identified during these verifications should be implemented without delay.
5.3 Employees‘ equipment
It is necessary to ensure that the facilities, equipment or accessories required by the personnel are in a proper condition and that the personnel are instructed in their use.
Uniform, clearly identifiable working clothing assists the personnel in the fulfillment of their tasks and contributes to the avoidance of disputes in areas of potential confrontation.
Top of page
5.4 Prohibition of intoxicating substances
"The consumption of alcoholic beverages and the use of other intoxicating substances during working hours are [prohibited]. This also applies for a suitable period prior to the start of work. Employees must be sober when starting work." (4)
| 4 | § 5 Prohibition of intoxicating substances; Unfallverhütungsvorschrift BGV C7; Wach- und Sicherungsdienste of 1 October 1990, in the version of 1 January 1997; Hauptverband der gewerblichen Berufsgenossenschaften. |
5.5 Personal safety
Whenever conducting security-related activities, control personnel must pay attention to their own personal safety. Hazardous activities jeopardize not only the security objectives but also the life or physical wellbeing of the personnel involved.
5.6 Control of vehicle and pedestrian traffic
All movements of vehicles and individuals must be subject to the supervisory authority of the control personnel. Technology is only used in a supporting role. Unrestricted reliance on technology alone jeopardizes the security objectives.

Figure 9: Control of vehicle and pedestrian traffic, copyright: Rasthof Uhrsleben e.K.
Top of page
5.7 Administration of keys
It is recommended that the administration of all keys giving access to security-related areas be implemented using a professional key management system based on DIN 77200 (Security services), Section. 4.15.
5.8 Conduct of controls and patrols
The staffing of the gate building forms the basis for the security of all other control personnel. The gate building must therefore be staffed at all times, without exception, by at least one employee. This employee’s tasks include the security monitoring of check-in/check-out operations in the gate area and the alerting of assistance services if required. The gate building must always be kept closed. Access is permitted to authorized persons only.
Control personnel working in the parking area (for example during patrols) who are not involved with check-in/check-out operations in the gate area should always be equipped with a radio device and maintain radio contact with the gate building. It would also be desirable to additionally equip personnel with an electronic personal security system.
The operational reliability and integrity of the fencing should be verified by means of security inspections conducted at irregular intervals at different times of day.
| Explanation The protection of the control personnel by the employee in the gate building permits a rapid, appropriate reaction in the event of attacks on the control personnel. This ensures that the police and emergency services are alerted immediately. |
5.9 Truck park regulations
If the processes employed at the truck park are to run smoothly, they must be defined in writing. In this regard, particular attention should be paid to:
| Compliance with the parking bay markings | |
| Observance of the defined distances between the sides of the trucks | |
| Prohibition of rear-to-rear parking | |
| Prohibition of the use of cooking apparatus outdoors outside of properly demarcated areas | |
| Cleanliness |
It is necessary to implement the truck park regulations consistently and perform regular checks to ensure they are observed.
| Explanation It is necessary for trucks to be parked in accordance with the parking bay markings in order to implement the surveillance concept. It prevents, for example, CCTV cameras being blocked by parked vehicles. Clean truck parks reduce the opportunity for criminal activity since discarded objects cannot be used to assist in offences. |
Top of page
5.10 Staff regulations
Staff regulations are required to cover all normal operating processes as well as emergencies or interruptions to normal operation. These must be available to employees in written form. They provide employees with certainty in the performance of their duties and protect them against incorrect behavior, in particular in unusual situations.
These staff regulations may cover, for example:
| Contact with clients | |||
| Conduct of entry and exit controls | |||
| Visitor management, for example: |
|||
| External companies carrying out maintenance and cleaning work | |||
| Emergency services | |||
| Fire service | |||
| Police |
|||
| Control measures | |||
| Documentation | |||
| Reporting instructions | |||
| Conduct in response to special incidents | |||
| Response on the failure of technical equipment | |||
| Emergency plans | |||
| Emergency calls | |||
5.11 Access regulations for personnel
Employees should enter and leave the high-security area exclusively via the baffle gate systems. This regulation should also be observed by senior management personnel in order to provide a positive example. In general, employees‘ private vehicles should not be allowed access to the high-security site.
Top of page
5.12 Checking in arriving trucks
This involves, for example, the following activities:
| Check for placed parking bay reservation | |||
| Check of personal identities using personal identification document or passport and photocopying of these | |||
| Digital photograph or still image from CCTV recording (at an image resolution sufficient to permit unambiguous identification) of the drivers together with the front of the vehicle and the official vehicle registration plate. | |||
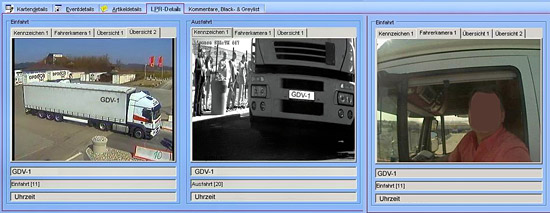
Figure 10: Still image from CCTV recording together with official registration plate, truck, driver
Copyright: Autohof Wörnitz GmbH & Co. KG
| Documentation (digital photograph or still image from CCTV recording) of the trucks from all sides, including all official vehicle registration plates for the purposes of QM assurance. The underside of the vehicle is exempt from this requirement. | |||
| Sealing of all openings in the vehicle superstructures | |||
| Issuing of personalized access cards for the baffle gate systems (see Section. 3.11 Individual passage of persons) to the vehicle crew. These cards are valid for a restricted period only. | |||
| Detailed written documentation, for example: |
|||
| Date and time of arrival | |||
| Numbers of seals |
|||
| Payment transaction, if possible cashless using customer card etc. | |||
| Notification of arrival to the reservation center | |||
| All documentation should be stored for at least one year | |||
| Explanation The comprehensive control of both trucks and drivers together with complete documentation of the drivers and crews and the associated vehicles reduce the opportunity for potential criminals to commit crimes in the high-security truck park, increase driver safety, protect control personnel against avoidable dangers and also protect the truck park operator against incalculable risks. |

Figure 11: Attaching a seal to the customs seal string, copyright: Rasthof Uhrsleben e.K.
Top of page
5.13 Checking out departing trucks
This involves, for example, the following activities:
| Check of personal identities using personal identification document or passport with consultation of photocopies made on arrival | |||
| Comparison of the existing digital photographs and still images from the CCTV recording with the individuals and trucks | |||
| Check of seals on all sides and comparison with the documentation (digital photographs) | |||
| Digital photograph or still image from CCTV recording (at an image resolution sufficient to permit unambiguous identification) of the drivers together with the front of the vehicle and the official vehicle registration plate and all the sides of the vehicle together with all official registration plates. The underside of the vehicle is exempt from this requirement. | |||
| Collection of all personalized access cards for the baffle gate systems | |||
| Detailed written documentation, for example: |
|||
| Date and time of departure | |||
| Integrity of the seals applied on arrival |
|||
| Notification of departure to the reservation center | |||
| All documentation should be stored for at least one year | |||
| Explanation See explanation in 5.12 (Checking in arriving trucks) |

Figure 12: Documentation during truck check-in/check-out:
copyright: Rasthof Uhrsleben e. K.
Top of page
5.14 Transshipment
In the event that semi-trailers, trailers, swap bodies or containers are to be exchanged or temporarily deposited in the high-security truck park then the truck park operator should be notified of this in advance.
Such prior notification should contain, for example, the following information for both the arrival or departure of the transport container that is to be exchanged:
| Full address of the haulage company and details of how and when to access it | |
| First names and surnames, dates of birth and, if possible, digital photographs of the truck crew | |
| Expected date and time of arrival, for example, together with the planned period of presence | |
| Official registration plate of the towing vehicle | |
| Official registration plates of the semi-trailer and trailer | |
| Official registration number of the vehicle chassis and identification number of the swap container when swap bodies or containers are exchanged |
The exchange, depositing or retrieval of semi-trailers, trailers, swap bodies or containers without prior notification should be prohibited.
The high-security area should possess specially demarcated zones for transshipment operations. If possible, these should be clearly separated by fencing from the other parking areas in accordance with Section. 3.2 (Fencing), paragraphs 1 and 2. Furthermore, the security requirements relating to high-security truck parks also apply accordingly in this area.
During the check-in of arriving trucks for transshipment purposes, it is particularly important to identify the means of transport and the drivers and to establish the authorization for the delivery of the means of transport. Alongside the examples set out in Section. 5.12 (Checking in arriving trucks), the objectives concerning protection can be achieved as follows:
| Counter-check of the data of the driver performing the delivery and the delivery vehicle itself with the data present in the prior notification with regard to the authorization to hand over the container. | |
| Verification of the identity of the transport containers that are to be exchanged (in the case of swap bodies, for example, by checking the official chassis number and the identification number). | |
| Special marking of such transport containers, for example by means of specially colored seals in order to simplify the check-out of departing trucks. |
During the check-out of departing trucks for transshipment purposes, it is particularly important to identify the means of transport and the drivers and to establish the authorization for the acceptance of the means of transport. Alongside the examples set out in Section 5.13 (Checking out departing trucks), the objectives concerning protection can be achieved as follows:
| Counter-check of the data of the driver retrieving the container and the retrieval vehicle itself with the data present in the prior notification with regard to the authorization to accept the container. | |
| Verification of the integrity of the special markings | |
| Verification of the identity of the transport containers that are to be exchanged (in the case of swap bodies, for example, by checking the official chassis number and the identification number). |
Integrity checks of deposited transport containers should be performed at regular intervals and at different times of day.
| Explanation For the purposes of the present requirements, at least two means of transport are involved in a transshipment operation. These exchange their transport containers at a previously agreed location. The increased effort during the check-in/check-out of arriving and departing trucks is necessary in order to minimize the risk of releasing deposited containers to unauthorized persons. |
Top of page
5.15 Reservation of parking bays
In so far as can be planned in advance, parking bays in high-security truck parks should be reserved in advance.
Flexible parking bay management with a reserve stock of bays must be implemented in order to cope with specific driver situations such as excess fatigue, sudden illness, rest periods that cannot be postponed etc.
| Explanation Thanks to the possibility to pre-book truck parking places, the participating freight carriers and haulage contractors can reliably plan the itineraries of cargoes at risk of theft. |
5.16 Data protection
Security-related and organizational measures should be designed in such a way that they do not impinge upon the privacy of truck drivers or infringe their rights in the matter of data protection.
| Preference for low-interference measures If possible, instead of CCTV surveillance, a greater distance should be observed between the sides of the vehicles in accordance with Section 2.2.2 (Parking bays / markings). In sensitive areas with regard to data protection and areas with lower security requirements, CCTV surveillance should be employed as a less intrusive alternative to CCTV recording. |
|
| Adoption of the principle of necessity Measures with data protection implications – such as CCTV surveillance and recording – should only be used if they are genuinely required in order to achieve the intended objectives (e.g. exclusion of routes to catering and sanitary facilities). |
|
| Guarantee of the principle of dedicated use Recorded CCTV data/personal identification data may only be used for the purpose of investigating criminal activities. As the body responsible for the data, the truck park operator is entitled to communicate this data only to the criminal investigation authorities. Under no circumstances should it be possible for third-parties, for example employers, to obtain access to personal data. |
|
| No threat to the privacy of truck drivers Since truck drivers spend at least part of their spare time in their vehicles and also spend the night there, the space in the driver’s cab forms part of their private lives. This space should be excluded from CCTV surveillance. If this is not possible then the privacy of drivers must be ensured by means of other technical/organizational measures. |
|
| Indication of CCTV surveillance Appropriate and clear notices must be employed to indicate the use of CCTV surveillance and recording. Furthermore, the body responsible for CCTV surveillance must indicate storage period and the purpose of CCTV surveillance. The fact that CCTV images will be made available to the responsible police department in the event of criminal activity must also be clear in the displayed notices. In addition, the corresponding information can also be printed on the back of the truck park tickets. |
|
| Storage period The storage period for CCTV recordings and identity-related data depends on the length of time this data is required in order to fulfill the purpose for which it was stored. A storage period of approximately 30 days is recommended. If the subsequent deletion of this data is prohibited due to a statutory retention period then the data may continue to be stored in a form locked against access until the expiry of this period. The possibility of using pseudonyms or storing the data in anonymous form should be considered. |
| Top of page | Contents |
